Cybersecurity Essentials: Protecting Your Business From Digital Threats
by Abdul Aziz Mondal Business Security Systems Published on: 01 June 2023 Last Updated on: 24 May 2025

Businesses use technology to streamline operations and attract a broader audience in today’s digital world. However, greater reliance on technology comes with the risk of cyber threats, which can jeopardize sensitive information and harm a company’s brand.
Cyber-attacks are becoming more sophisticated and frequent, emphasizing the critical need for more robust cybersecurity measures. Hackers are finding new ways to penetrate systems and steal sensitive information as technology progresses, making it more critical than ever to be cautious and secure in our online activities.
As a result, cybersecurity is no longer a choice for any firm seeking to protect itself from digital dangers. In this blog post, we’ll go over some crucial cybersecurity tips and methods your firm should be aware of to protect itself from intrusions.
What Is Cybersecurity

Protecting your organization from cyber threats through effective cybersecurity procedures is critical in today’s digital landscape for maintaining the safety and integrity of your sensitive information and operations.
Malware, phishing assaults, and ransomware are examples of such risks. Cyber assaults may inflict considerable financial and reputational harm to enterprises of all sizes, making cybersecurity a top priority for businesses.
Effective cybersecurity entails establishing various measures, such as network security, email security, and personnel training, to lower the chance of a cyber attack and mitigate its damage if one occurs. Businesses may preserve their assets and reputation by taking cybersecurity seriously while increasing customer trust and confidence.
Businesses of all sizes must be aware of the risks posed by cybercrime and adopt protective measures. Here are a few of the reasons why cybersecurity is critical for every business:
Cyber Attacks Are Becoming More Sophisticated
Cyber-attacks are becoming more complex and challenging to detect as technology progresses. Organizations can incorporate OT asset inventory as a critical security practice to adequately protect against these emerging threats. This preventative approach entails extensively examining and identifying all operational technology (OT) assets within a network, including industrial control systems and sensors, and compiling a detailed inventory.
Organizations can gain a better understanding of their network, as well as measures like cyber threat hunting that they could implement in order to detect any flaws that cyber attackers could exploit.
A Breach Can Come With A Significant Cost.
According to IBM Security and the Ponemon Institute, the global average data breach cost is now $3.86 million. This amount covers direct expenses like notifications, fines, and legal bills, as well as indirect costs like lost customers, reputation damage, and missed business prospects.
Cybersecurity Is Now Regulated By Law
With the implementation of GDPR in 2018, data protection is now governed by law throughout Europe. Businesses must now have proper technical and organizational measures to secure client information or risk incurring significant fines and other penalties.
Maintaining The Trust Of Your Customers Includes Keeping Their Data Secure.
Customers rely on businesses to safeguard their personal and sensitive information, which can result in severe financial and reputational harm. Effective security asset management is one method of ensuring data security.
Common Types Of Digital Threats
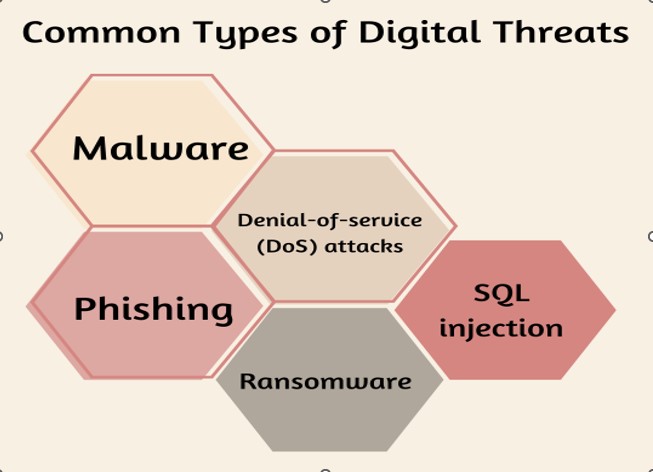
Businesses today confront a wide range of digital dangers. The following are some of the most common:
Malware
Malware is malicious software that is meant to destroy or impair computer systems. It poses a severe threat to both individuals and companies. It is transmitted via email attachments, webpages, and other internet resources.
Phishing
Phishing is internet fraud that involves duping consumers into giving personal or financial information. It usually happens through email or rogue websites.
Denial-Of-Service (Dos) Attacks
A denial-of-service (DoS) attack attempts to interrupt access to a computer or network resource, making it inaccessible to its intended users and creating substantial disruption and inconvenience. This can be accomplished by flooding the target with requests, forcing it to crash.
SQL injection
SQL injection attacks allow hostile actors to execute damaging code on a database server by exploiting software vulnerabilities, resulting in data breaches, system damage, and compromising user privacy. This can be used to steal data or update the database without the owner’s authorization.
Ransomware
Ransomware is a virus that encrypts a user’s files and then demands a ransom in exchange for the decryption key. This attack can cause data or financial loss and might be challenging to recover from.
Tips And Tricks For Protecting Your Business From Digital Threats
The threats to businesses are increasing as the world gets more digital. Cybersecurity is critical for all businesses, regardless of size or sector. Here are some pointers to help safeguard your business against digital threats:
Keep Your Software Up-To-Date
Keeping your software up to date is one of the best methods to defend your company against digital attacks. One of the most popular ways for hackers to get access to a system is through outdated software. You can help patch any existing vulnerabilities by keeping your software up to date.
Educate Your Employees
Another strategy to safeguard your company from cyber dangers is to educate your personnel on the best cybersecurity procedures. Teach them how to recognize phishing emails, set strong passwords, and contribute to the security of the company’s data. The more knowledgeable your personnel are about cybersecurity, the less likely they will be attacked.
Use Two-Factor Authentication
Two-factor authentication (2FA) is another excellent technique to secure your data. 2FA adds protection by demanding a second verification form, such as a fingerprint scan or a code texted to a mobile device, before granting access to sensitive data. This makes gaining access much more difficult for hackers, even if they have gained a password or other login credentials.
Implement Good Cybersecurity Practices Across All Devices and Networks
Reasonable cybersecurity measures must be implemented across all devices and networks. This includes using strong passwords, keeping antivirus software up to date, and watching for strange activities. For organizations aiming to stay ahead of evolving threats, selecting the best threat intelligence platform is vital, as it can provide a comprehensive view of the current threat landscape and recommendations for defense.
Invest In A Security Solution
Finally, investing in a security system can dramatically reduce your exposure to digital dangers. Numerous options exist, including firewalls, antivirus software, malware protection tools, and web filtering solutions. Investing in the proper solution for your company can help safeguard it against criminal actors that want to exploit your data or infrastructure.
Conclusion
Protecting your organization from cyber dangers is critical in today’s digital world. You can protect your data, keep hackers out of the system, and maintain the security of all parties involved by investing in cybersecurity solutions and using best practices such as encryption and strong passwords.
Implementing an effective cybersecurity plan is one of the most excellent methods to safeguard your company from potential cyber threats. You may assist in protecting your company’s information and provide a safe environment for employees and customers by implementing appropriate protections and training. While no security system is perfect, having the appropriate technologies in place can help prevent cyberattacks and protect your company’s reputation.
FAQs
Q: What Are Cybersecurity Essentials?
A: Cybersecurity Essentials is a comprehensive guide that helps businesses protect themselves from digital threats. It covers a range of topics, including threat assessment, risk management, and incident response planning.
Q: Who Can Benefit From Cybersecurity Essentials?
A: Cybersecurity Essentials is designed for businesses of all sizes and industries. It benefits small and medium-sized businesses without dedicated IT staff or resources to manage cybersecurity.
Q: What Are Some Of The Topics Covered In Cybersecurity Essentials?
A: Cybersecurity Essentials covers a range of topics, including network security, email security, password management, mobile device security, and employee training.
Read Also: