5 Cybersecurity Threats that Emerged in 2020 – How to Protect Your Company
by Abdul Aziz Mondal Business Security Systems Published on: 03 December 2018 Last Updated on: 27 May 2025

Each year, even as efforts are being made to fortify defenses against cybersecurity threats, hackers seem to be a step ahead. Like the preceding years, 2018 saw its share of more advanced strategies that cybercriminals are using to hack into the systems of companies and steal information. The past year has certainly seen a number of cybersecurity threats.
Should this Factor Worry You?
It should, given that 19% of customers will stop shopping at a store that has had a data breach incident. And that’s not all; at least 33% of consumers will avoid visiting the business establishment for an extended period of time. Should you check this feature on Business Insider, you will learn that affected businesses include retail outlets, restaurants, grocery stores, fitness centers, and electronics chains, to name a few.
As all business owners are aware, not only is it mandatory by the law that you disclose details of the breach to your consumers and vendors, but you also risk lawsuits that they may bring against your company. These are only a few of the fallouts of a successful cybersecurity threat. Studies have shown that at least 60% of small companies that have faced data breaches are unable to sustain the losses and are likely to shut down within 6 months. If you are the owner of one of the 70% of small enterprises most vulnerable to cybercrime, here are some of the potential threats you should take steps against.
Here are 5 Cybersecurity Threats that Emerged in 2020 – How to Protect Your Company
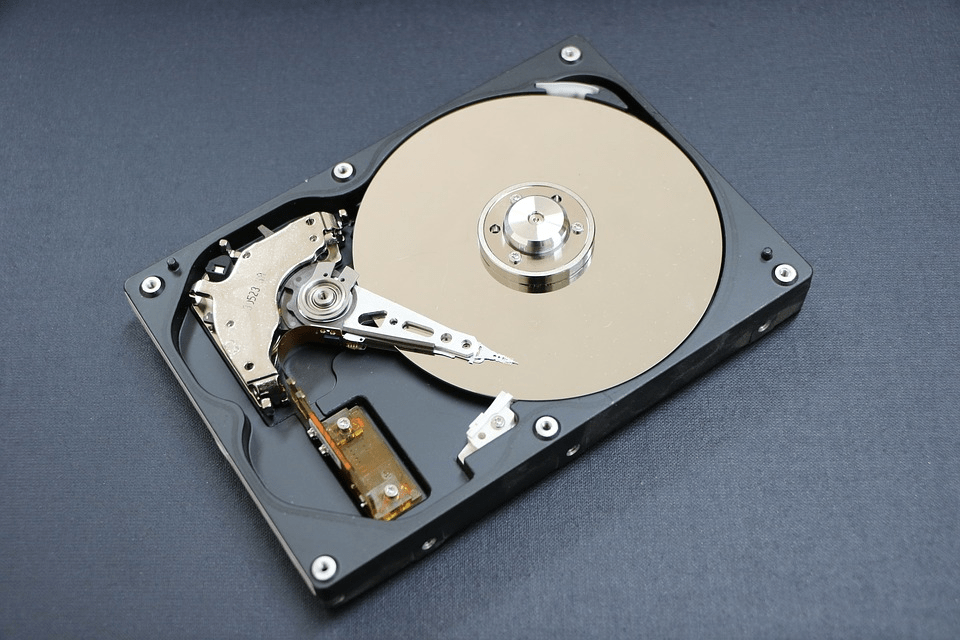
1. Data Harvesting from Old Hard Drives:
In today’s time when companies cannot function without a range of electronic equipment, you need to keep a close watch on the devices and gadgets used in your establishment. That’s because old drives packed with sensitive data act as easy channels for cybercrime threats. Hackers can buy off the drives from internet portals like eBay to harvest the Personally Identifiable Information (PII) they can use.
When you’re ready to upgrade to new equipment, sign up for the services of certified agencies like All Green Electronics Recycling for data wiping and overwriting services. Entrust your old gadgets to these agencies, and they will use government protocols to ensure that the data in the Hard Disk Drives (HDDs) and Solid State Drives (SSDs) are disposed of securely. The solutions they use are carefully designed to make it impossible for the most sophisticated hackers to retrieve any data on your drives. If needed, the agency will shred the drives and provide you a certificate of indemnification.
2. Artificial Intelligence (AI) to Decipher Passwords:
One of the most potent of cybersecurity threats that have emerged is the use of AI to get targeted entities to reveal their passwords and other security details. AI is highly efficient at mimicking humans to send fake phishing messages and convince users to download malware and give up sensitive information. Like Steve Grobman, chief technology officer at McAfee reveals to MIT Technology Review, “AI, unfortunately, gives attackers the tools to get a much greater return on their investment.” He goes on to warn people about how AI is more adept at dodging the security systems that are designed to spot malware before it infects company networks.
Your best bet to secure your enterprise is to get the latest security solutions with the help of agencies that conduct regular audits and advise you on how to upgrade your defenses.

3. Using Computer Capacity for Crypto mining:
Mining for bitcoins may not exactly fall under the category of cybercrime threats because you don’t need to worry about losing sensitive information. Nor will you have to worry about attacks like denial of service or Ransomware. Instead, you stand to lose computing capacity. Crypto mining needs a high amount of processing power to make the complex calculations to mine Bitcoin. Hackers getting into your systems use them without getting detected.
You may only notice that the networks function more slowly, or that you lose battery power faster than estimated. Devices needing upgrades and replacements sooner than their average life expectancy is another loss you may incur. The more worrying factor is that crypto-jacking tools are available on the dark web for just $30 as reported by this study on CSO Online and have the potential to generate a high return on income. To protect your company, work with the IT team to install antivirus and host endpoint protection software that detects the crypto-miner code. Getting anti-crypto mining and ad-blocking extensions for your company’s web browsers is also a smart move.
4. Taking Control of the Internet of Things (IoT):
As in most homes and workplaces, it is not uncommon to have all the devices connected to a single server via the internet. Accordingly, you may have computers, printers, copiers, thermostats, and various other office appliances controlled remotely that are all a part of the Internet of Things (IoT). While this facility spells huge convenience, it also opens up a host of vulnerabilities for potential hackers.
Greg Nichols reports to ZNet that in the coming years, an average workplace is estimated to have around 24,762 devices. According to a survey conducted by the Ponemon Institute, 97% of the respondents admitted that a cybersecurity threat to their IoT could have disastrous effects on the working of the organization while 60% talked about their concerns about not having the necessary defenses against Ransomware.
Being aware of the company’s vulnerabilities is the right first step toward building a robust security system. Your IT team is likely to advise you best on how to plug the gaps and set up the necessary firewalls to keep your business protected.
5. Phishing Using legitimate-looking Web Pages:
Developing rogue web pages that mimic legitimate websites and entice users to give up their passwords is another cybercrime threat that every business should be aware of. The year 2018 saw a 65% rise in such phishing attacks with at least 76% of companies talking about how they became victims. Here is an example that displays a Google sign-in page that looks exactly like the real thing. The best you can do is to educate your employees about rogue pages like these and to be wary about where they add their passwords.
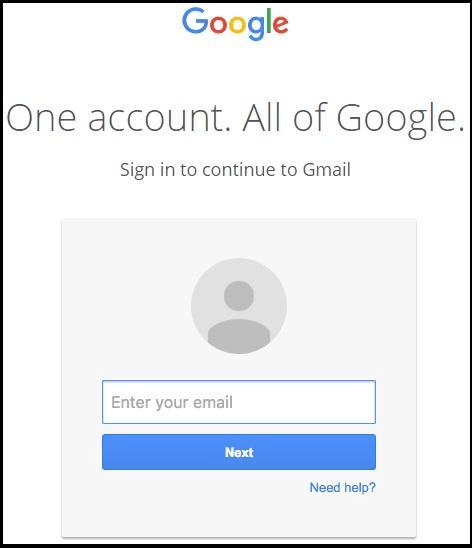
Figure 1 – Source PCMag
Cybersecurity threats are a real menace and with the advance of technology, you can expect to come across more sophisticated forms that put your business at risk. Your best defense is to remain informed of every form of the menace as it emerges and take the necessary steps to mitigate the risks.
Read Also: